After we have created our oracle compute virtual machine our next goal is to get our application installed on those virtual machines. Applications sitting on different virtual machines need to talk to each other internally too. For this internal connection we need to open ports between those machines.
For our application In this post we will open communication between the two instances on a specific port 50 and will enable a telnet service. After opening the ports on the VMs we will verify if we are able to telnet from one instance to the other on that specific port 50
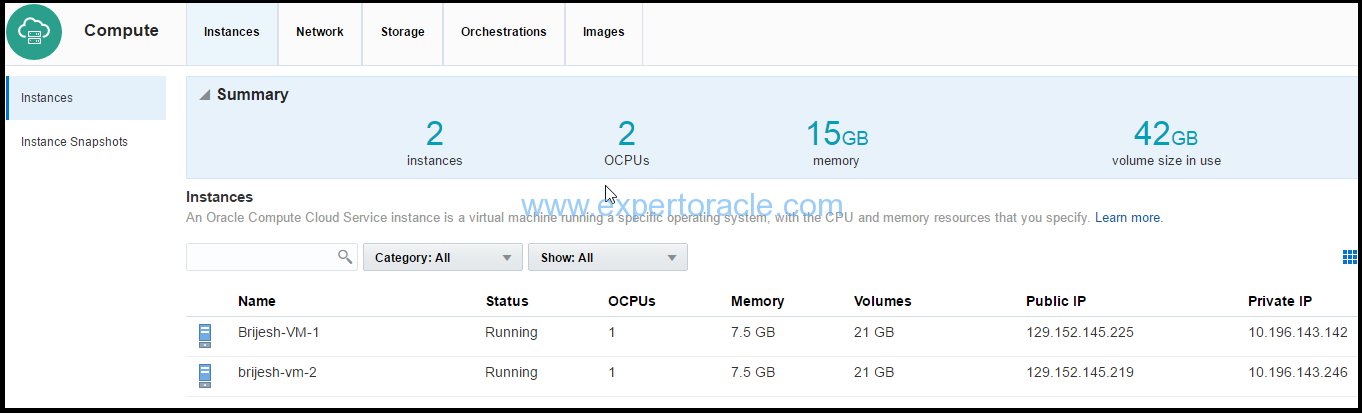
We have two virtual machines already created
High level steps
1) Create two security lists
2) Add both instances to the security lists
3) Create Security application to open port 50
4) Create a security rule
5) Verify the port using telnet
1) Create two security lists
We will be creating two security lists, one each for our virtual machines.
1. On the Oracle Compute Cloud Service console, click the Network tab.
2. Click the Security Lists tile, and then click Create Security List.
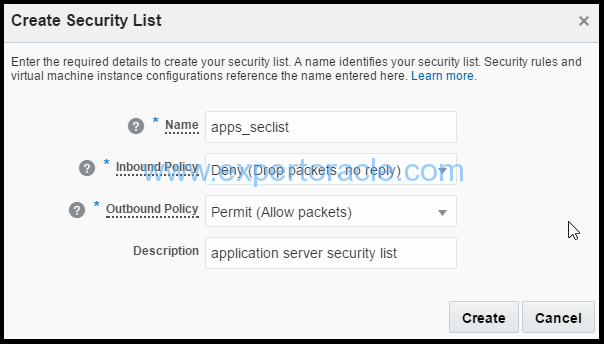
3. In the Create Security List dialog box, select or enter the following information, and then click Create.
a. Name: Enter an appropriate name. For the purpose of this tutorial, enter apps_seclist. b. Inbound Policy: Retain the default policy; deny (Drop packets, no reply). c. Outbound Policy: Retain the default policy, Permit (Allow packets). d. Description: Enter an appropriate description, if required.
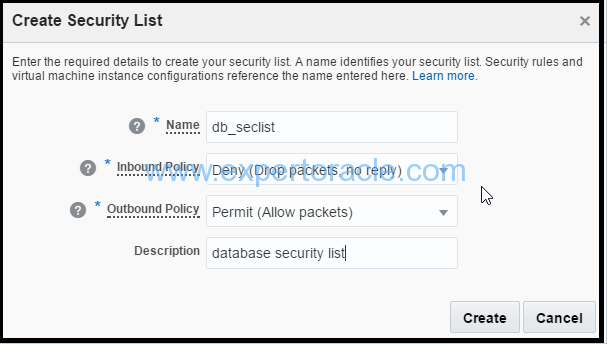
Similarly follow step 1-3 above and create another security list with below values
2) Add both instances to the security lists
We will be adding our first virtual machine Brijesh-VM-1 to the application security list > apps_seclist
We will be adding our second virtual machine Brijesh-VM-2 to the database security list > db_seclist
a) On the Oracle Compute Cloud Service console, click the click the Instances tile.
b) Go to the instance Brijesh-VM-1, and from the menu, select View.
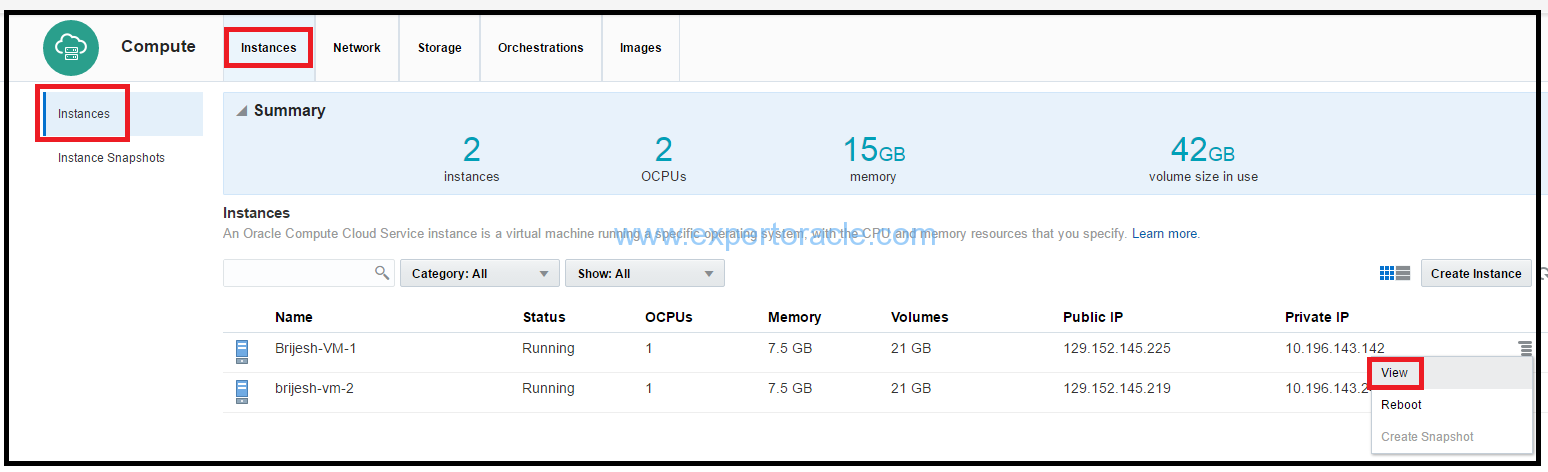
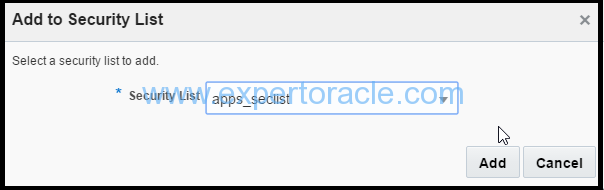
c). In the instance details page, click Add to Security List. Select the security list apps_seclist that you just created, and then click Attach.
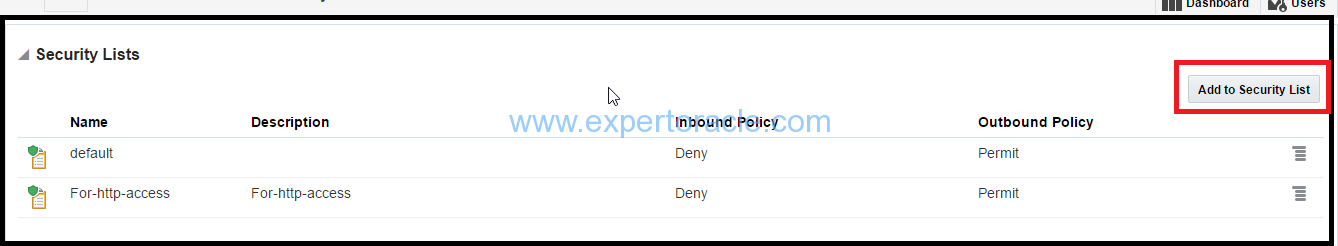
d). Remove the “default” security list attached to the VM instance
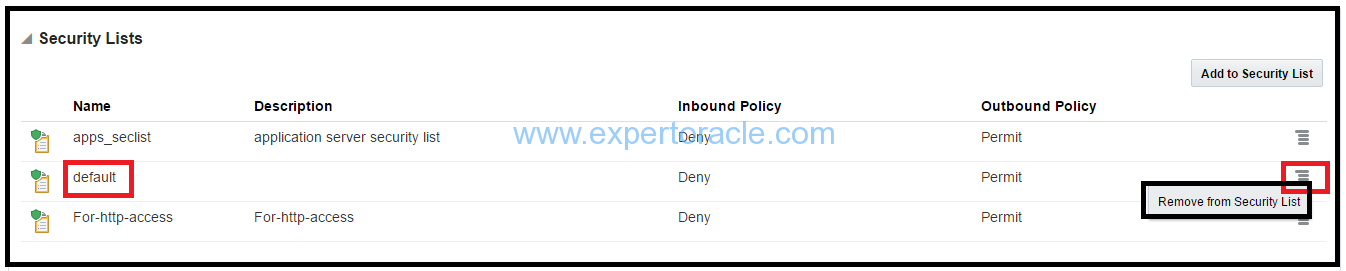
e) Your instance is added to the apps_seclist security list.
Similarly follow step (a)-(d) above and add db_seclist to Brijesh-VM-2 virtual machine.
3) Create Security application to open port 50
A security application, in this context, is a mapping between a port number and port type (TCP, UDP, or ICMP). To open port 50, we must first create a security application for that port in Oracle Compute Cloud Service.
a) Sign in to Oracle Cloud My Services and navigate to the Oracle Compute Cloud Service console.
b) Click the Network tab and then the Security Applications tile.
c) Click Create Security Application.
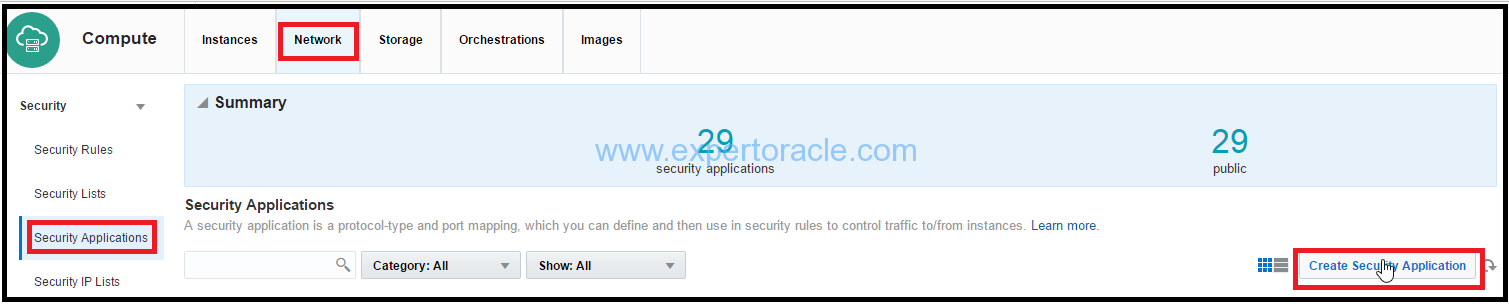
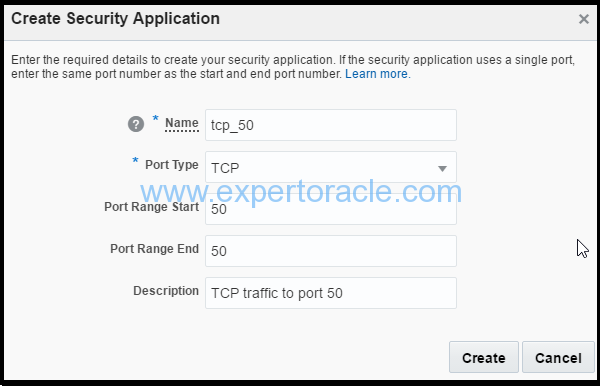
d) In the Create Security Application dialog box, input the following information
o Name: Enter a name for the new security application (for example, tcp_50). Note this name. You'll use it later in this tutorial. o Port Type: Select tcp. o Port Range Start and Port Range End: In both these fields, enter the port that you want to open (for example, 50). o Description: Enter a description for the new security application (for example, TCP traffic to port 50).
4) Create a security rule
Next, create a security rule to permit traffic over port 50 from the Oracle Compute Cloud Service instances from one instance to the other.
1. Sign in to Oracle Cloud My Services and navigate to the Oracle Compute Cloud Service console.
2. Go to the Network tab.
3. Click the Security Rules tile.
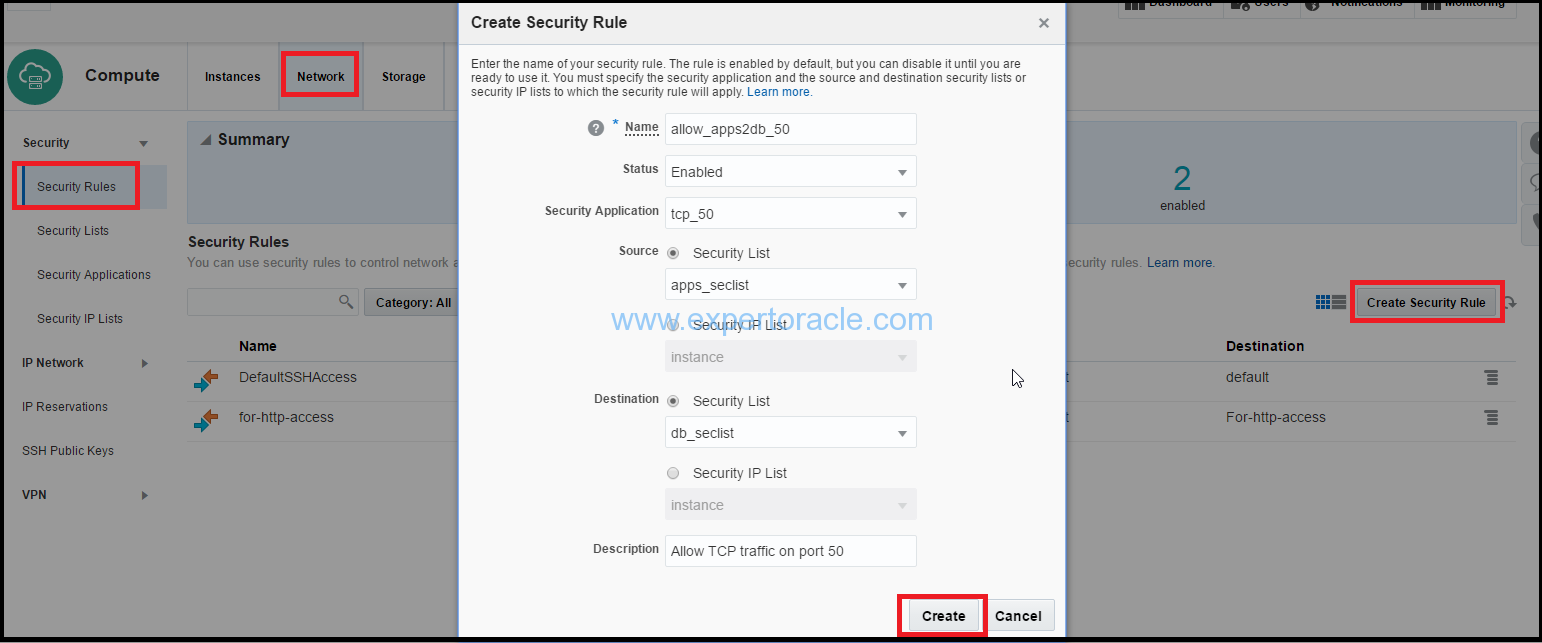
4. Click Create Security Rule, and provide below information:
Name: Enter a name for the rule (for example, allow_apps2db_50). Status: Select Enabled. Security Application: Select the tcp_50 security application that you created earlier. Source: From the security lists drop-down list, select apps_seclist. Destination: Select db_seclist. Description: Enter a description for the rule (for example, Allow TCP traffic on port 50 ).
5). Click Create.
TCP traffic can now flow on port 50 from your source instance that is part of the ms_seclist security list to the destination instances that are part of the db_seclist security list.
5) Verify the port using telnet
Now you should be able to telnet from your source (apps_seclist) telnet VM to destination (db_seclist) telnet VM and should get a login prompt
$ telnet <Private IP_address_destinationVM> 50
Trying 10.196.143.246…
Connected to 10.196.143.246.
Escape character is ‘^]’.
Oracle Linux Server release 6.4
Kernel 3.8.13-118.9.2.el6uek.x86_64 on an x86_64
login:
- Oracle Multitenant DB 4 : Parameters/SGA/PGA management in CDB-PDB - July 18, 2021
- Oracle Multitenant DB 3 : Data Dictionary Architecture in CDB-PDB - March 20, 2021
- Oracle Multitenant DB 2 : Benefits of the Multitenant Architecture - March 19, 2021


Nice explained. Could you guide me how to change listener port from 1521 to 1530 in DBaaS?